
ERM - Enterprise Risk Management

t-Risk was developed to support corporate security risk managers in their integrated risk analysis and security planning. It is an analytical tool that helps in the identification, analysis and assessment of risks. In other words, it covers the entire process that occurs between data collection and risk management planning.
The t-Risk platform uses a deconstructive method, as it transforms a large and difficult problem into small problems. It will help you find solutions that harmonize property security with business development, acting to reduce the vulnerabilities that affect the critical success factors (FCS) and objectives of your organization or client company.
Click in one of the projects, the user will find the menus of the large work blocks:
Customers, Parameters, Risk Assessment and Settings.
In the Customers block, customer data are registered and your projects. The system shows the updated comparison of performance indicators.
In the Parameters block, the user provides information on monthly invoicing, number of employees, existing controls (resources) etc. Following the instructions, the user defines the risk profile of the organization, the profiles of the evaluators and the weight that each one will have in the allocation of values.
These two blocks, Customers and Parameters, gather the data for the setting the context. In them, for example, the Critical Success Factors of the Reference System (company or organization) and the risk tolerance profile obtained from the customer are informed. In a later step, the system will show whether the controls will leave the Reference System (company or organization) within the risk tolerance profile indicated by the customer.
The Risk Assessment block is dedicated to identifying, analyzing and evaluate the state of the Reference System, in relation to property security, and define the appropriate security controls. By filling in the data, the user will complete the following assessment modules: Risk level; Risk x Risk Matrix; Matrix Critical success factors; Existing control x Necessary control; Reduction of expected loss; SWOT matrix; Action plan; and Completion report.
By clicking on one of the projects, the user will find the menus of the main work blocks:
Clients, Parameters, Risk Assessment, and Settings.
In the Clients block, client data and their projects are registered. The system shows an updated comparison of performance indicators.
In the Parameters block, the user provides information about monthly revenue, number of employees, existing controls (resources), etc. Following the instructions, the user defines the organization's risk profile, the evaluators' profiles, and the weight each will have in assigning values.
These two blocks, Clients and Parameters, gather the data to establish the context. For example, they include the Critical Success Factors of the Reference System (company or organization) and the risk tolerance profile obtained from the client. In a later stage, the system will show whether the controls will keep the Reference System (company or organization) within the risk tolerance profile indicated by the client.
The Risk Assessment block is dedicated to identifying, analyzing, and evaluating the state of the Reference System regarding asset security, and defining the appropriate security controls. By filling in the data, the user will complete the following assessment modules: Risk Level; Risk x Risk Matrix; Critical Success Factors Matrix; Existing vs. Required Control; Expected Loss Reduction; SWOT Matrix; Action Plan; and Completion Report.
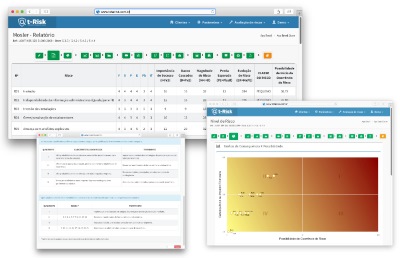
Risk level
The establishment of the risk level begins with the Mosler method, which deals with the factors involved in a given risk with the least possible subjectivity. The Mosler method is based on six criteria, which are assigned weights from 1 to 5, depending on the degree of influence. These are the criteria: function, substitution, depth, extent, probability and financial impact. More details are provided by tutorials on t-Risk.
Weight allocation may require the work of a consultant in conjunction with people who know the SR in depth. In such cases, it is recommended to set up a small committee with representatives from different areas of the client company. The more diverse the profiles, the more balanced the weights will be. The weights given by the consultant may be worth two or three times higher than the others. It is recommended that there be one or more evaluators for every 500 employees. T-Risk records and points out the degree of reliability of the assessment.
Still using the Mosler method, the system creates four new columns in the table: importance of success, damage caused, magnitude of risk, expected loss and risk evolution.
Risk evolution (ER) leads to the classification of risks in order of importance for the organization''s objectives and Critical Success Factors.
Right next, t-Risk shows the Risk Level matrix, of four cells, with the relationship between the risk factors and their consequences.
This matrix leads to two tables: the first one contains recommendations for treatment and the second shows how the risk classification would look with the treatments indicated.
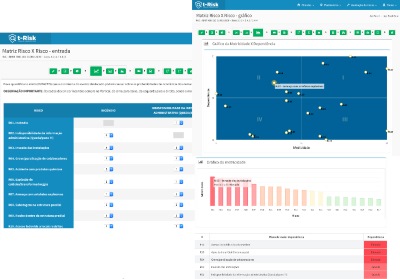
Risk x Risk Matrix
In this block, the user assigns weights to the degree of influence that each risk has over the others. T-Risk calculates the motricity of a risk to drive other risks and the dependence on each one. Tutorials and explanatory tables guide the step by step for the user to reach the Risk x Risk matrix, an important element of analysis.
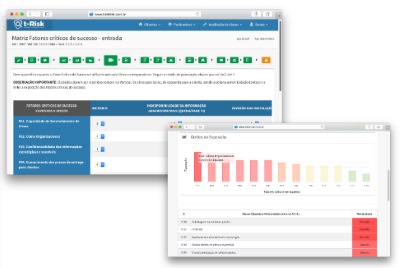
Critical success factors Matrix
To quantify the degree of influence of each risk on Critical Success Factors, the user assigns weights ranging from zero (no influence) to four (high influence). In return, the system produces tables and graphs that demonstrate the vulnerability of each Critical Success Factor listed.
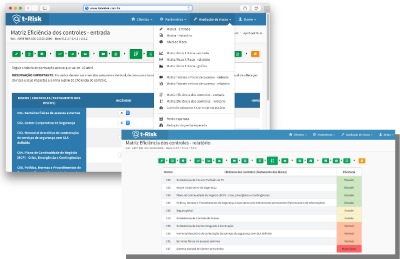
Existing control and necessary control
The user assigns points to reduce each risk in the presence of controls. The points range from minus 10 (big reduction) to zero (no change). The system issues a report on the efficiency of handling risks, with tables and graphs. The results form the basis for the next step, which is the grading of controls into levels.
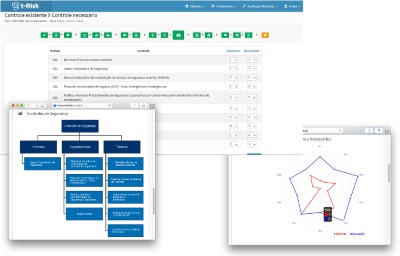
The system generates a highly informative graph comparing the existing controls with the necessary controls.
A table with the security controls, in its three modalities (human, organizational and technical) guides the user as to the recommendations that he should make to his client.
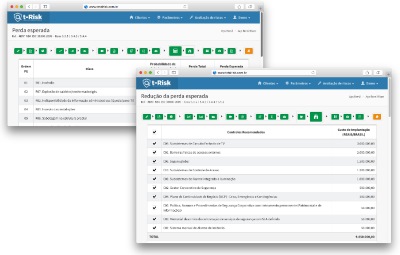
Reduction of expected loss
New table informs the expected loss in cash, which provides an estimate for the volume of effort and capital to be invested in the controls for each particular risk.
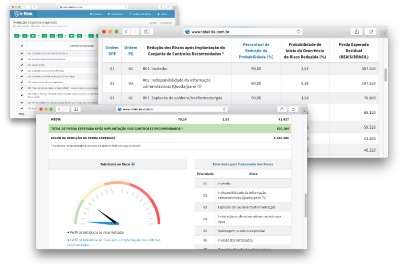
In the next step, the expected loss reduction values are obtained after implantation of the recommended controls - RPE. T-Risk spells out investment priorities, with cash values. The decrease in expected loss allows the client to reason about ROI in risk mitigation.
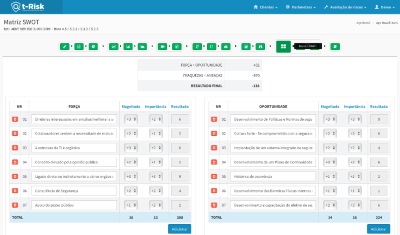
SWOT Matrix
A SWOT matrix helps the user to see the best ways to take care of controls and points of attention.

Action plan
In this step, the user applies his expertise to make his recommendations regarding the actions to be taken. External physical barriers, alarm system, closed circuit television, access control, policies, standards, procedures, electronic systems are some of the most efficient security features known.
The first risks to be addressed can be those with very high motor skills and very high dependency. The destination of investments, however, will be decided by the client.
However the action plan may be, there will always be residual risks. To eliminate the risk for good, it would be necessary to eliminate the generating activity.
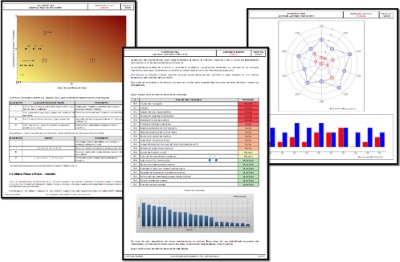
Final report
Finally, the system generates a report
Use Cases

Corporate Security Director (Contractor)
- Companies need to hire consultants to provide a corporate security risk assessment or update old assessments.
- Usually a lot of time is lost in meetings informing the needs of the company and what methods to use.
- You tell them what you want and you have no idea what the final report will look like as each consultant has their own approach and reporting pattern.
- Create a user on the t-Risk Platform and ask the consultant(s) to use this ISO 31000-based process. By doing so, you automatically prevent them from changing your methodology and criteria. You can even provide an assessment template (which is already provided in the system) to show the level of quality you expect.
- t-Risk allows you to create assessments that can be updated at any time.
- Schedule a periodic review and require consultants to do this on the t-Risk Platform.
- Manage, monitor and compare the evolution of Risks centrally through the risk indicator management panel.
- Hire consultants based on their experience and always stick to the t-Risk risk analysis method and reporting standard.
- Create Risk Scorecard, providing an executive view of Risks, including indices and metrics that facilitate the establishment of criteria and support decision-making.
- Manage the treatment of risks, prioritizing the controls that have the best cost-benefit ratio.
- Manage threats, vulnerabilities and controls in a collaborative and decentralized way, in a web environment.

Asset security service and solution providers (Surveillance & electronic security company)
- Your contracting clients periodically request risk assessment, the preparation cost is high, the team is not specialized and the method used is not similar to the risk assessment methods used by the contracting party. If your company serves in several states and /or countries, adds complexity as there will be multiple internal analysts using divergent methods and presentations.
- Another recurring fact is the charges due to claims and damages occurring within the customer's facilities that are imputed to the service provider. Often the customer does not know their risks and your company is unable to objectively present the risks existing in the contracting client, the possible impacts and adequate way to deal with these risks.
- Your customers indicate that your proposal and way of selling is too commercial and not very technical. You need to increase the level of convincing and sales arguments based on real risks and potential impacts.
- Create risk assessment standards specific to your company. Your team will save up to 80% time in creating a complete risk assessment with automatic reporting. Updating a report is simple and very fast.
- The entire team will use the same risk assessment standard based on the international standard ISO 31000 and the reporting standard will always be the same.
- If your client has a claim that had already been identified in their risk analysis and the indicated controls were not implemented, it will be easier to defend themselves and avoid unnecessary losses with claims arising from risks accepted by the client.
- Develops preliminary risk analyzes to support its commercial proposal and increase sales in a grounded and defensible way based on the risks identified in the client company.
- Surprise your customers with commercial proposals based on the customer's own risks and increase sales of services and technologies.
- Create a Risk Scorecard for your client to monitor in real time, providing an executive view of Risks, including indices and metrics that make it easier to establish criteria and support decision-making.
- Manage threats, vulnerabilities and controls in a collaborative and decentralized way, in a web environment. Your entire team will work using exactly the same risk analysis model.
- Provide comparative metrics and benchmarking of the evolution of the risk management process of your client's organization. They will perceive much more value in your service, if positively differentiated from the competition.

Security Consultant
- Your contracting clients periodically request risk assessment, the preparation cost is high, the team is not specialized and the method used is not similar to the risk assessment methods used by the contracting party. If your company serves in several states and /or countries, adds complexity as there will be multiple internal analysts using divergent methods and presentations.
- Another recurring fact is the charges due to claims and damages occurring within the customer's facilities that are imputed to the service provider. Often the customer does not know their risks and your company is unable to objectively present the risks existing in the contracting client, the possible impacts and adequate way to deal with these risks.
- Your customers indicate that your proposal and way of selling is too commercial and not very technical. You need to increase the level of convincing and sales arguments based on real risks and potential impacts.
- Create risk assessment standards specific to your company. Your team will save up to 80% time in creating a complete risk assessment with automatic reporting. Updating a report is simple and very fast.
- The entire team will use the same risk assessment standard based on the international standard ISO 31000 and the reporting standard will always be the same.
- If your client has a claim that had already been identified in their risk analysis and the indicated controls were not implemented, it will be easier to defend themselves and avoid unnecessary losses with claims arising from risks accepted by the client.
- Develops preliminary risk analyzes to support its commercial proposal and increase sales in a grounded and defensible way based on the risks identified in the client company.
- Surprise your customers with commercial proposals based on the customer's own risks and increase sales of services and technologies.
- Create a Risk Scorecard for your client to monitor in real time, providing an executive view of Risks, including indices and metrics that make it easier to establish criteria and support decision-making.
- Manage threats, vulnerabilities and controls in a collaborative and decentralized way, in a web environment. Your entire team will work using exactly the same risk analysis model.
- Provide comparative metrics and benchmarking of the evolution of the risk management process of your client's organization. They will perceive much more value in your service, if positively differentiated from the competition.

Suppliers (Supply Chain and Third Party Companies)
- Its suppliers are contractually obliged to assess their risks, issue periodic reports and do not have the capacity or knowledge to perform this obligation.
- They do risk assessment to fulfill contractual obligations, but they use different criteria than your company. What your company considers high risk may be low risk for them. Therefore, they may not have to report certain risk to your company. company or manage it as the contract requires.
- As your suppliers do not have the capacity to prepare risk assessments, your company needs to hire consultants to prepare risk assessments in the companies that make up your supply chain.
- Define your risk criteria so that your suppliers follow the process defined in the t-Risk Platform.
- Keep records and evidence in a single point of control, gathering all useful information in the same database.
- Create a model risk assessment and define the areas you want vendors to address (minimum standard).
- Assess results in real time, request evidence and explanations of threats, impacts, vulnerabilities, probabilities and risk controls.
- Have your suppliers periodically and quickly update previous evaluations within the period defined by your company.
- Follow the evolution of your supply chain risks.
- Provide benchmarking and benchmarking of risk evolution and risk management process for your entire supply chain.
- Unify all your supply chain comparative reports and dashboards to support your organization's management and decision-making.
- Standardized, structured third-party security risk assessments that quickly identify and enable you to prioritize risk treatment.
- Get vendors to complete their own security risk assessments and let you review them in real time, freeing up your staff for other essential activities.
- Standardize risk assessments according to the international standard ISO 31000 ensuring they are defensible.
- More assurances that contractual obligations related to supply chain risks are being properly addressed, decreasing your own organization's residual risks.
- Compare your supply chain risk indicators with your own risk profile.

Professor and Trainer of Security Risk Management
- You have a lot of knowledge and experience in several areas of private property security, corporate security, but you don't have a consolidated method for analyzing and evaluating risks. You may never have needed to prepare risk assessments.
- Practically all subjects in the discipline or course are within your domain, but risk management is a new area of knowledge in the corporate security sector and you do not have the methodological experience to teach this subject.
- Consider using the t-Risk Platform as a method for risk analysis in your courses or subjects taught.
- Use the t-Risk logic, which is based on the ISO 31000 International Standard, to guide your students through the risk management process quickly, simply and at no cost, using the free version for students and teachers.
- Use t-Risk together with the ISO 31000 standard itself to further increase your students' satisfaction level.
- The process is so simple and logical that your students will catch on quickly.
- Increase the quality of your class by obtaining higher levels of learning by forming more qualified professionals.
- If you are also a security consultant, you can offer services using t-Risk as per the above Security Consultant use case.

Student and beginner in security risk management
- No experience in security risk management.
- Does not know effective methods to assess risks professionally.
- The traditional way (Word, Excel, Power Point and PDF) is a lot of work and takes a lot of time.
- Ensure methodological rigor in all risk assessments, with repeatable processes based on the international standard ISO 31000.
- Use data libraries to store your own content and create replicable models for every type of customer or market segment, speeding up the process for all future assessments.
- Use impressive interactive charts and other visual aids to present reports and risk indicators to your clients, demonstrating seniority and valuing their work.
- Develop your skills based on an internationally known standard – ISO 31000.
- Save up to 80% of time compared to the traditional way of preparing risk analysis.
- Your client will be able to manage and monitor the evolution of Risks through the web in real time, adding value to your work.
Best practices for managing risks
The t-Risk Platform follows international best practices for managing corporate security risks.
What is the international standard ISO 31000 and what is it for?
The ISO 31000 Standard is a set of principles to be followed in order for risk management to be efficient, consistent and effective. It is a guidance document for organizations to implement and develop integrated risk management systems.
It was designed to be applied by any type of organization (private company, public company, community entity, association, group or even individual), in the most different actions, such as decisions, strategies, operations, processes, functions, projects, in addition to management of products, services and assets.
Increasingly, companies are establishing formal risk management processes. Using ISO 31000 as a basis for the analysis of practices and processes is to manage risks by identifying them, analyzing them and evaluating them according to the organization's risk criteria.
The application of ISO 31000 brings direct and indirect benefits, since the systematic, transparent and reliable management of risks affects the operation of the entire company. The benefits start with establishing the context, directly linked to the understanding of the organizational objectives, the internal and external environments, the stakeholders and what risk means for each organization in particular.
The ISO 31000 Standard directly addresses the needs of these stakeholders:
- those responsible for developing the risk management policy;
- those responsible for ensuring that risks are effectively managed;
- those who need to assess an organization's effectiveness in managing risk;
- developers of standards, guides, procedures and codes of practice.
Risk management guided by ISO 31000 enables the organization to solidify the pursuit of its objectives, inspire proactive management, pay attention to risks throughout the organization, better identify its threats and opportunities, adhere to international standards and regulatory requirements, improve its governance, minimize losses, and many other benefits.